In this review we will go over Elgato Key Light ecosystem according to the Unwanted Cloud methodology to determine whether it is usable without giving away your data, and whether it respects your privacy.
Although our review will use the Key Light Air, this review also applies to the other key lights that Elgato sells.
The Elgato Key Light range is very conscious of your privacy and is an excellent choice for a smart controllable key light.
A
Overall rating
Cloud requirements
The Elgato Control Center app is available on the Android and Apple play store. When launching the app for the first time, we are guided through the initial pairing process. The app has no concept of user accounts, all you have to do is to connect it to your WiFi.
The key light is controllable when your phone is connected to the same WiFi network as the light. All lights on your network are automatically discovered. One thing to keep in mind is that everyone on your network will be able to control the lights.

A
Cloud requirements
Data portability
The app or website does not have any dedicated data export, but there is practically no configuration to export aside from the lights name and current settings. There are also no user accounts.
A
Data portability
Ecosystem openness
The Elgato Key Light can be controlled locally using a REST API without any cloud connection. See this blog post for API details and this library for a reference implementation. As mentioned previously, the API does not have any authentication, it’s open to all users on your network.
A
Ecosystem openness
Data privacy
Elgato has a general Privacy Policy, however there is no links to it from the Android app. Via the Apple app store listing, we can see that the app collects some data, however no data that is linked to you.
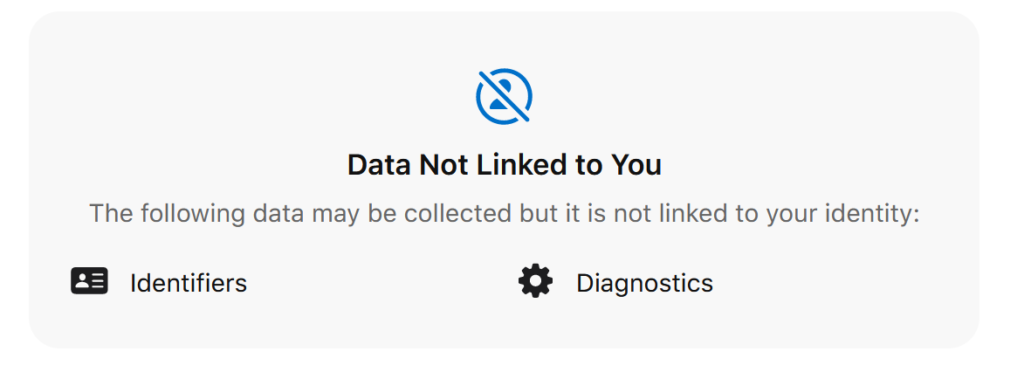
Considering the absence of an account system, we have no reason to doubt this information.
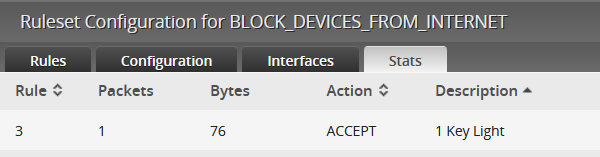
We observed that upon startup, the Elgato Key Light Air does briefly communicate over the internet. However, the amount of data is very small and we have no reason to believe that any persistent tracking is occuring.
A
Data privacy
Tested on Android using version 1.0 of the Unwanted Cloud methodology.


Leave a Reply